邻居认证使得路由器确认每次所收到的路由更新的源。如果关键字不匹配,就会拒绝路由更新。
Cisco使用两种类型的邻居认证:纯文本和MD5.
纯文本认证发一个关键字,这个关键字是明文传输,可被非法用户所窃取,所以不推荐使用。
MD5认证发一个报文摘要,而不是关键字。MD5被用来生成一个关键字的散列。这个散列是被发送的对象。MD5方式不易被非法用户所窃取。
这个案例中,我们在R1与R2之间使用明文认证,在R2与R3之间使用MD5认证。
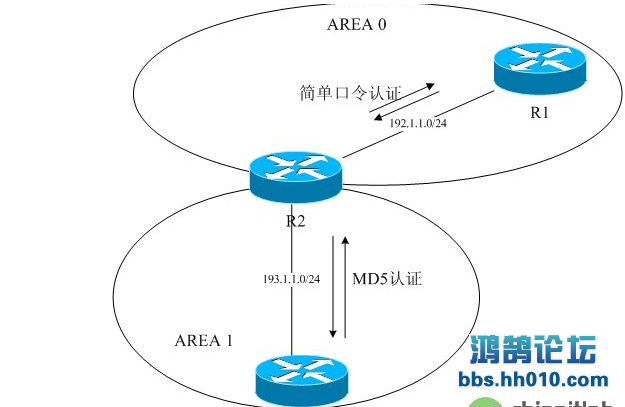
| [pre]// R1 //int e0/0 ip ad 192.1.1.1 255.255.255.0 ip ospf authentication-key cisco //明文认证,关键字为ciscorouter os 1 network 192.1.1.1 0.0.0.0 area 0 area 0 authentication[/pre] |
| [pre]// R2 //int e0/0 ip ad 192.1.1.2 255.255.255.0 ip ospf authentication-key cisco //明文认证,关键字为ciscoint e1/0 ip ad 193.1.1.2 255.255.255.0 ip ospf message-digest-key 1 md5 crackerrouter os 1 network 192.1.1.2 0.0.0.0 area 0 network 193.1.1.2 0.0.0.0 area 1 area 0 authentication area 1 authentication message-digest[/pre] |
| [pre]// R3 //int e1/0 ip ad 193.1.1.3 255.255.255.0 ip ospf message-digest-key 1 md5 crackerrouter os 1 network 193.1.1.3 0.0.0.0 a 1 area 1 authentication message-digest[/pre] |
验证过程:
| [pre]r1#sh ip os int e0/0Ethernet0/0 is up, line protocol is up Internet Address 192.1.1.1/24, Area 0 Process ID 1, Router ID 192.1.1.1, Network Type BROADCAST, Cost: 10 Transmit Delay is 1 sec, State BDR, Priority 1 Designated Router (ID) 193.1.1.2, Interface address 192.1.1.2 Backup Designated router (ID) 192.1.1.1, Interface address 192.1.1.1 Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:06 Index 1/1, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 1 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 193.1.1.2 (Designated Router) Suppress hello for 0 neighbor(s) Simple password authentication enabledr2#sh ip os int e0/0Ethernet0/0 is up, line protocol is up Internet Address 192.1.1.2/24, Area 0 Process ID 1, Router ID 193.1.1.2, Network Type BROADCAST, Cost: 10 Transmit Delay is 1 sec, State DR, Priority 1 Designated Router (ID) 193.1.1.2, Interface address 192.1.1.2 Backup Designated router (ID) 192.1.1.1, Interface address 192.1.1.1 Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:04 Index 1/1, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 2 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 192.1.1.1 (Backup Designated Router) Suppress hello for 0 neighbor(s) Simple password authentication enabledr2#sh ip os int e1/0Ethernet1/0 is up, line protocol is up Internet Address 193.1.1.2/24, Area 1 Process ID 1, Router ID 193.1.1.2, Network Type BROADCAST, Cost: 10 Transmit Delay is 1 sec, State DR, Priority 1 Designated Router (ID) 193.1.1.2, Interface address 193.1.1.2 Backup Designated router (ID) 193.1.1.3, Interface address 193.1.1.3 Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:03 Index 1/2, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 2, maximum is 2 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 193.1.1.3 (Backup Designated Router) Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 1r3#sh ip os int e1/0Ethernet1/0 is up, line protocol is up Internet Address 193.1.1.3/24, Area 1 Process ID 1, Router ID 193.1.1.3, Network Type BROADCAST, Cost: 10 Transmit Delay is 1 sec, State BDR, Priority 1 Designated Router (ID) 193.1.1.2, Interface address 193.1.1.2 Backup Designated router (ID) 193.1.1.3, Interface address 193.1.1.3 Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:04 Index 1/1, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 2 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 193.1.1.2 (Designated Router) Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 1[/pre] |
// R3 //debug ip ospf adjint e1/0 ip ospf message-digest-key 5 md5 crackerr3#01:16:03: OSPF: Rcv pkt from 193.1.1.2, Ethernet1/0 : Mismatch Authentication Key - No message digest key 1 on interface01:16:09: OSPF: Send with youngest Key 5r3#show ip ospf neighbor //观察结果无法发现邻居。//认证未通过,无法与R2建立起邻居关系。 当我们把MD5认证KEY改回1后,认证通过。
第二步实验,我们把关键字进行修改:
// R3 //debug ip ospf adjint e1/0 ip ospf message-digest-key 1 md5 cuijian01:21:33: OSPF: Rcv pkt from 193.1.1.2, Ethernet1/0 : Mismatch Authentication Key - Message Digest Key 101:21:40: OSPF: Send with youngest Key 1 我们要在实际工作中学会使用debug这个思科排错的利器。 |