題庫有錯,191答案應該是A,C+ Y1 C. U" Q1 i; x
 9 g* s8 t+ A2 d* M: K' f u4 `, C
9 g* s8 t+ A2 d* M: K' f u4 `, C
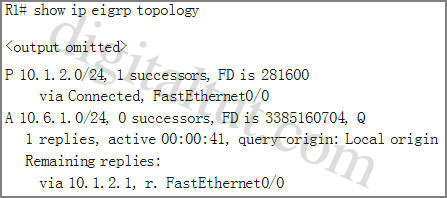
Refer to the exhibit. Which tworeasons for IP SLA tracking failure are likely true? (Choose two.) A. A route back to the R1 LANnetwork is missing in R2 B. The default route has wrongnext hop IP address C. The destination must be 172.30.30.2for icmp-echo D. The threshold value is wrong E. The source-interface isconfigured incorrectly Answer: A, E Explanation: If “source-interfaceFastEthernet0/0” is used, the routing table of R2 should have a route back toR1 LAN network in order to solve the IP SLA tracking failure. If the routing table of R2 doesnot have a route back to R1 LAN network, the “source-interface FastEthernet0/0”is configured incorrectly. Remove the portion “source-interfaceFastEthernet0/0” or use “source-interface FastEthernet1/0” instead would solvethe IP SLA tracking failure. The setting of the defaultroute has no effect on the IP SLA tracking for “icmp-echo 172.20.20.2” since R1routing table has a directly connected routing entry of 172.20.20.0/30.
N% l# L+ h4 u% B" _* i% z7 Z
8 X4 r- G0 V: T/ b" u3 SA network engineer enables OSPFon a Frame Relay WAN connection to various remote sites, but no OSPF adjacenciescome up. Which two actions are possible solutions for this issue? (Choose two.) A. Ensure that the OSPF processnumber matches among all remote sites B. Configure the neighborcommand under OSPF process for each remote site C. Change the network type tononbroadcast multipoint access D. Change the network type topoint-to-multipoint under WAN interface E. Enable virtual links Answer: B, D Explanation: Since OSPF usesRFC NBMA mode on Frame Relay WAN interface by default, the “neighbor” commandis required under the OSPF process for each remote site.
! P! @8 s9 ^. z/ ?0 b# Z- lOn the other hand, you couldalso change the network type to point-to-multipoint mode by typing the command “ip ospf network point-to-multipoint” under theFrame Relay WAN interface. For RFC point-to-multipoint mode, no “neighbor”command is required. 6 w7 ]6 [8 G' {, M7 {6 t3 @
( {+ d% i/ ^* ~6 Z+ a |  简体中文
简体中文 英语
英语
 日语
日语
 韩语
韩语
 法语
法语
 西班牙语
西班牙语
 越南语
越南语
 泰语
泰语
 阿拉伯语
阿拉伯语
 俄语
俄语
 葡萄牙语
葡萄牙语
 德语
德语
 意大利语
意大利语
 希腊语
希腊语
 荷兰语
荷兰语
 波兰语
波兰语
 保加利亚语
保加利亚语
 爱沙尼亚语
爱沙尼亚语
 丹麦语
丹麦语
 芬兰语
芬兰语
 捷克语
捷克语
 罗马尼亚语
罗马尼亚语
 斯洛文尼亚语
斯洛文尼亚语
 瑞典语
瑞典语
 匈牙利语
匈牙利语
 繁体中文
繁体中文
 文言文
文言文







 发表于 2017-2-20 17:06:55
发表于 2017-2-20 17:06:55
 置顶卡
置顶卡 喧嚣卡
喧嚣卡 变色卡
变色卡 千斤顶
千斤顶 楼主
楼主

 准备考试了 能确认下标准的嘛
准备考试了 能确认下标准的嘛