|
上个月通过NP买的会员还没到期,有近期要考135的可以参考下,以下是3月10号的更新,后续有会及时更新 Question 1 Which statements about uRPF are true? (Choose two) A. CEF should be enabled8 f, z. I( Y& T
B. CEF should be disabled
5 T6 d. O* @6 Y2 X) NC. Packet with source 0.0.0.0 destination 255.255.255.255 will be permited
! T! H+ U4 N6 t2 N1 R3 P- B' lD. Packet with source 0.0.0.0 destination 255.255.255.255 will be denied4 l3 c. M' X8 h# R2 {8 C4 F
E. ?
W( A5 [8 W; p9 }/ p5 fAnswer: A C Explanation uRPF uses the Cisco Express Forwarding (CEF) Forwarding Information Base (FIB) to perform reverse path look-up on the source IP address of an incoming packet. The CEF FIB is a database of network layer routing information and associated forwarding/adjacency information used in the CEF switching of packets. Unicast RPF will allow packets with 0.0.0.0 source and 255.255.255.255 destination to pass so that Bootstrap Protocol (BOOTP) and Dynamic Host Configuration Protocol (DHCP) functions work properly. Question 2& H" n( P! e, |; c; b q
Routes are not advertised in the GRE tunnel. What is the problem? A. Implement dynamic routing in tunnel interfaces; @+ Z/ D. X2 ~4 J
B. ACLs are blocking packets
7 u$ ~7 r. T/ m; FC. ?
6 [/ ]: P& m$ c4 k% Z, l# ND. ? ; a5 y& r; _ |8 ?6 }
Answer: B Question 3- y5 ^' M: ^1 J0 d& N( ^9 J: E d
How can we limit the number of simultaneous access to the VTY lines? A. session-limit
% }; l1 A+ _1 v" g% E# }B. something about ACL
. P$ w5 G# i+ L4 @4 Q# [C. ?. e2 B% L" s$ D5 [
D. ?
# q+ _0 x ^4 b/ k* p1 D9 {5 bAnswer: A Explanation The “session-limit” command is used to configure the maximum number of the concurrent virtual terminal sessions on a device. The range is from 1 to 64. Question 4
A+ L5 R6 p3 L$ }7 r. g6 b Drag drop question which includes: TTL, df-bit, ToS, Timeout. Maybe similar to this question: D&D Question on Extended Ping Answer:$ j' v, O& U; F$ k/ |' Y
Tos – …quality of service: E4 c4 g; f) G; r) X r1 @
Df-bit – prevent packets from being segmented or broken up( o6 l* e( {+ ~7 Y
Data pattern – detect framing errors/ t) m" ?' v# Z4 J! _
Hop count – verify routing metrics
6 |/ U/ {# G1 aReply – verify reachability OR data pattern — troubleshoot framing errors7 f+ E9 r; j; m; Z6 L' V
df-bit — enable do not fragment bit in IP header/ Z0 C. G( r, H/ G% o1 w
source — specify source address or name
- y3 b: ]2 X- R7 f! ~! {tos — specify type of service value
/ ~. E- u" U3 Avalidate — validate reply data Good reference: Question 5
+ W) t! W3 B' K- ^" o What command can be used to troubleshoot GRE issues? A. show dmvpn& {1 o0 \& c0 r0 I; P" p0 Y
B. show ip interface brief
- o9 D% \* r, K4 kC. show ip route
, r# s, m% V- p6 Y5 H8 C9 mD. ?
5 R: M! D$ @1 \* n5 uAnswer: A Question 6
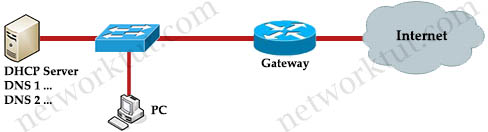
/ W# p# v, R8 U: s6 O5 A Refer to the exhibit. PC was not configured to obtain default-gateway from the DHCP server. What can we do for PC to access the Internet? A. Configure static ARP in gateway router) Z3 L) j( S- n, _' u! Y S$ D
B. Configure dynamic ARP in gateway router
; U! m6 e4 g& k1 R" W/ s CC. Configure proxy-ARP in gateway router
' z3 d5 B0 Y2 E; t5 N" @D. ? ; z: F) I/ T; J, w" w, _' @. L) F- z; g
Answer: C Question 7
! z2 X( y1 M# I2 L0 W3 W, B1 ~ Exhibit of a tunnel configuration of either side was shown. Only difference was:. W4 v7 u5 ^5 _4 E9 @) d
tunnel-mtu 1440 | tunnel-mtu 1476
; G7 y. E- R" g, _What is the issue? Question 8
6 |& F' e u: z Question about “show debug condition” command. Refer to the exhibit. Router#show debug condition! y$ Y) M+ D: o2 d* A" R* k
condition 1: int g0/1 …5 L5 u! s0 x7 x, N
condition 2: int g0/2 …' v+ m/ e! |% `& {
Router##no debug condition 1 |
What is the output of “show debug condition “? A. Router#show debug condition
5 F# @. R" H3 J; Scondition 1: int g0/1 …
1 [! L. D+ M. ? K m; ]condition 2: int g0/2 …. {% G. e% Y: e9 u
B. Router#show debug condition
, u9 ?7 S9 R( Ucondition 1: int g0/2 …/ B6 w% ] Q' W. J' N
C. Router#show debug condition# L7 Q ?! k: T; S: D2 d" W
condition 1: int g0/1 …
, y: v) \: {8 ]; P- d5 b! i0 n, SD. Router#show debug condition% s* H/ v w6 D' B
condition 2: int g0/2 …
( Q# {$ B5 U: l" j4 JAnswer: D
: C+ m* R3 L/ @7 ~2 H. F1 s Explanation We tested it with IOSv15.4 and this is the result:
5 f0 h# C' n4 [8 i G. E- P" v8 K
; R- C( v" N8 |9 V( j! _补充内容 (2019-3-14 08:12):" @; E$ }$ N+ G* \- ~$ Z
Question 9& C# [* Q5 b; z' E( V" J- a% v2 P
, b( h" K" [0 ?; S3 RRefer to exhibit. Client unable to enter the privilege mode
/ G* ]7 K" h- H( g8 L1 _/ ^( X; {! V6 V$ K1 A* ^3 V# i
. I* D5 M+ p" j$ w1 ?. L/ {/ }" b) z; Q0 e
Answer: enable password should be configured, [: e5 C; q' ~
" Y& b% }2 N- t: s7 q
Question 10
7 e$ ^1 ~" F0 t1 d" i/ p
5 W7 y7 N7 }- {9 M7 i) h0 [ {Refer to the exhibit.2 C; d3 t* Q8 _& E/ W; T( Q6 M
! W: U/ G h( o$ ^<exhibit missing> u8 Y5 P1 a \4 Q7 n7 h
D! v: w8 h6 `! a8 y+ C
Which statement is true for IPv6 access list commands(refer to exhibit).! w3 c0 ~1 l' F: U! x
+ S! s9 ^* |9 p& G' C' t2 o 9 j. C1 t( o: ?
2 C/ B8 p6 q6 C# \0 j
Answer: deny ipv6 any any log( l4 | O! N3 Y# ^, }
, M! H' O5 _$ dQuestion 11
9 d' I8 J$ J4 h4 n. S
' r) t! M. k5 I7 QSimilar to this question:
1 X% B4 O7 f# j( z5 Y- O; E) `6 \6 C" A- c6 {* \
Refer to the exhibit. (ClientA is connecting to the network via e0/0 interface while the “tunnel source e0/1” in the configuration). ClientA is unable to reach ClientB while other users from other Spokes can reach ClientB. Which command resolves this issue?! v y0 ^- Z. w& m" K, E
$ }( A/ O- |8 ^' RA. tunnel route-via ethernet0/1
8 n/ t+ y1 [1 p: U9 |$ VB. tunnel mode gre
$ }3 Q! X# D7 f4 y% }C. tunnel destination 10.100.0.1; B: F4 }5 w! h4 ~' g
D. tunnel source ethernet0/0# G# g ^) s$ i) g" d. N$ s
% u2 @# v2 v# v8 e# L1 ?0 o
$ L7 n p m" y7 A, v
$ [. j) m; g( Z6 b* J, V9 G5 A
Answer: D" P" S8 V$ d* ~* m! C# }
5 t/ m2 r% R. r9 E8 e, p' k( M8 G; P
Question 12
. @; [8 E& J: x* M3 Y7 T$ D8 T# B
1 M! A' d% K+ G' rRegarding extended ping, why ping is failed (refer to exhibit)?
9 p1 t4 `/ v7 e* h; X
: q- a& X/ ^% {& \
# {2 l$ \ V6 B! _9 L: @8 O5 l- F5 t9 P- T: A: J1 [) v8 z) O; ^, U
Answer: df bit is set (should be unset, mtu issue) |  简体中文
简体中文 英语
英语
 日语
日语
 韩语
韩语
 法语
法语
 西班牙语
西班牙语
 越南语
越南语
 泰语
泰语
 阿拉伯语
阿拉伯语
 俄语
俄语
 葡萄牙语
葡萄牙语
 德语
德语
 意大利语
意大利语
 希腊语
希腊语
 荷兰语
荷兰语
 波兰语
波兰语
 保加利亚语
保加利亚语
 爱沙尼亚语
爱沙尼亚语
 丹麦语
丹麦语
 芬兰语
芬兰语
 捷克语
捷克语
 罗马尼亚语
罗马尼亚语
 斯洛文尼亚语
斯洛文尼亚语
 瑞典语
瑞典语
 匈牙利语
匈牙利语
 繁体中文
繁体中文
 文言文
文言文







 发表于 2019-3-11 20:58:44
发表于 2019-3-11 20:58:44

 置顶卡
置顶卡 喧嚣卡
喧嚣卡 变色卡
变色卡 千斤顶
千斤顶
 楼主
楼主