本帖最后由 scorpio920204 于 2017-11-21 20:47 编辑 9 P& T6 f* s! h! L, R
P( z; G {' b+ QQuestion 1" Z2 p5 h( Q' j: n. b% C7 r
Whichtwo statements about NHRP in a DMVPN environment are true? (Choose two)! [/ X- @1 U) e C0 f4 z
a.It requires each endpoint to have a unique network ID
! Y8 z7 \ o$ M7 h# Ab. It routestraffic through the tunnel! u" P2 C# Q! I8 ]: Z" n, P6 @
c. It canidentify PIM-SM RPs over a tunnel1 a, ^. I v; s5 r0 Y- I
d. It canauthenticate VPN endpoints: s8 v/ v' H: y7 t3 E/ {" z
e.It provides address resolution to route traffic
0 j: m& V0 l8 n; \+ wanswer: D and E
/ J7 l5 U! A, x- L% |3 p---------------
7 a3 m8 Y7 l0 V V+ \Question 2
9 `: D+ v- |' D+ s4 _* x/ Y, X$ ]Whichtwo commands do you need to implement on the CALLING router to support the pppoeclient? (Choose Two)+ @7 m. N4 B- |& Z% ]6 [+ J6 E! s
A. peer default ipaddress pool! w2 N7 }$ l! R* Z7 j3 A- t
B. mtu
6 V, e0 u9 k: |9 y2 b% yC. bba-group pppoe
4 m* K3 h9 O9 X8 i) c: T% O# ?D. pppoe enable group: G6 n# D3 T6 A
E. pppoe-clientdialer-pool-number3 T4 _! ]7 v) t, d, W$ O1 o1 |3 h6 O
answer: B and E9 G# r2 i) `2 s* K5 S& @
---------------" S6 v5 a# O% E+ G& X. K
Question 3
3 ]+ Z; w% T+ q6 A1 f: R e2 P( O" Cwhat issupported radius server (choose two)7 L5 F* ^5 U# d* e, v \
A) telnet1 h+ m! x2 B) H# e, F- u. \6 v
B) authentication
0 W/ H4 {- p+ o% L5 N; G8 G3 UC) accounting
' h; F7 m& l/ f& d5 T4 fD) authorization
! I, c" \/ M' k# v, _E) SSH3 S: b3 m7 Q! H" s1 |, Y/ M
Answare: BD
. {: x! T2 I2 g. _8 P----------------# B6 @; p5 x2 E a% b
Question 4
' _$ g2 {( o* p) ZWhatfrom the following can cause an issue for URPF? (This could be single answer ormultiple choice)
) u1 Z t' Z) n4 G+ E9 iOR
" l! T Y& l% m1 f% [5 qReasons why urpf may fail:& X3 c2 {! W& ^% s7 o/ V
A.Assymetric routing
3 C% s% P6 E0 _! x0 FB.Cef not enabled% e3 t6 j! V5 X" R" }2 V
C.Urpf notapplied to the traffic source
0 s7 P% R2 A+ s( \ k% T: p; ~D.If it is usedas ingress filtering0 k5 U# W4 e( C# A, a7 i, E; J5 u# N
Answer: A
6 M. b. r, }# C% |( E----------------$ k& p8 Z, Z( p7 A. Q
Question 53 H' q/ H. o6 q3 {0 u- u# Q
Inwhich scenario can asymmetric routing occur?6 O0 R0 V4 x0 [' Y0 n" ?2 K
A. active / activefirewall setup
! w- k) R1 O7 ?( E Q2 C2 mB. singlepath in and out of the network.3 l- v9 m3 X1 q9 S+ d: Z
C. active / standbyfirewall setup8 f1 t" _* n- h
D. redundantrouters running VRRP! x4 l3 k4 e( l2 O7 E+ h9 v
Answer: D/ z: k' \2 Q, v# h( Y
---------------
: Z3 @0 S6 r7 N3 rQuestion 6 ! L& ?0 G% G; U
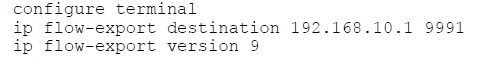
Referto the exhibit. How can you configure a second export destination for IPaddress 192.168.10.1?
0 b* ]3 M1 w' U- u; p! c4 [$ vA. Specify adifferent TCP port1 ~% @$ W+ G3 t1 J4 u5 i
B. Specify adifferent UDP port
0 s% b& P* E* tC. Specify a VRF: z! R( R: F8 F
D.Configure a version 5 flow-export to the same destination* b, c) ?0 F8 v y) \5 w
E. Specify a differentflow ID5 F: i5 J/ }: Z/ n1 ?0 D) L$ ?3 A
Answer: C
1 ], v; I; ^) u-------------
M8 x: P& @ s' m( iQuestion 7
* Z5 u+ B# ^' S1 _Configurationsnippet that looks similar to this:
9 n, l% e1 V4 T) o7 @ip access-list 1 permitxx xx @7 d6 f% n+ [/ L$ [# u* B6 A
ip natinside source list 1 int fa0 / 0 overload; l8 p J/ H& w4 _, h
What is this an exampleof?$ \# n/ b5 Q) F
A. static NAT
' j2 ^( B `4 B9 `5 D$ N) ^B. something about the ACL
) d, u4 W. }! {. CC. PAT4 N) E% X$ L( {
D. dynamic NAT
' H- h! m1 j% J# N qAnswer: C \0 i0 @) c, P4 }( } k1 d$ T! K
-------------% n; q0 D8 X' s! k" I# w
Question 8
/ T* _, ^+ l# D$ x; z/ F: Q) d- HTwolimitations when use NPTv6 for IPV6 to IPV6 Address translation?
2 P. a8 V' E9 Q' q$ t# {9 [A. stateful addresstranslation
0 @! V w+ m) e; j; Z1 ^& _/ h1 ~B. a limit of 321-to-1 translations
}7 O& g( I3 b" Q1 a6 ~9 t" N8 y8 M% YC. lack ofoverloading functionality
" \# L* A/ [5 R! o; U1 g! b- h- iD.identify all interfaceas NAT inside or outside
G" ]$ s5 u4 ^( J2 gE. 1-to-1 prefix rewrite
) i0 ^' U5 a/ wF. mismatchedprefix allocations
& y% R. z* v1 k2 y" Q- wAnswer: C E
2 y; a% r& ?, w2 X( e) Y------------ 1 o, {6 j6 p! {9 c( f6 K# u
) Y3 |9 Y; [8 N
Question 9/ [' @+ K, s9 y$ P
Theenterprise network WAN link has been received several denial of service attacksfrom both IPv4 and IPv6 sources. Which three elements can you use# L& c/ Q: ^: p
toidentify an IPv6 packet via its header, in order to filter future attacks?(Choose three)
! u5 O- n- B7 f' m# SA. Traffic Class, w. W* Q5 r- M0 z" l S
B. Source address3 @4 b* [3 b5 [ B, S9 z( U# S; i
C. Flow Label
& A0 t9 w' X7 O! V2 ]D. Hop Limit
6 y" [- v4 v- V0 k: v7 C1 SE. Destination Address& f* g, U- U8 o! n5 h
F. Fragment Offset9 `5 j6 v; h0 T) T0 K( E- g
Answer: A C D1 M5 m9 s9 s7 c6 `+ z0 f
------------8 S( V5 c0 L8 ?9 Z6 A j0 A( e
Question 10" t/ X9 \9 E' o& G( K- w
Considerthis scenario. TCP traffic is blocked on port 547 between a DHCPv6 relay agentand a DHCPv6 server that is configured for prefix delegation.
2 }7 P* L2 S. M0 f, DWhichtwo outcomes will result when the relay agent is rebooted? (Choose two)' Y+ Y9 Q" z( E: w9 G% c T$ b
A.Routers will not obtain DHCPv6 prefixes.
( J, \8 N/ N2 Y$ TB. DHCPv6clients will be unreachable.
! v) t0 f+ D; f; C: V5 yC. Hostswill not obtain DHCPv6 addresses. {0 i2 F: O' }
D.The DHCPv6 relay agent will resume distributing addresses.
5 ^5 t# [% T! E4 |- f2 [E.DHCPv6 address conflicts will occur on downstream clients.
2 ?5 D* f7 N l1 F/ ^ ^Answer: A C9 M8 i6 ~7 Z/ o! K6 L
------------' p/ H. _/ A' M. c+ @9 h4 \
Question 10" u' Y- y* |# i. o% k0 s7 J3 ?( Q
Whichcommand prevents routers from sending routing updates through a routerinterface?
9 T$ l. k& I3 y. T6 zA. default-metric 0
7 Z3 J Q& u5 ~- i# d1 jB. distribute-list in) t2 ~2 |: l. L \: t" {
C. passive-interface
5 f+ u) W) \* s6 w1 DD. distribute-list out
8 w: y! `. b5 k. ?1 z3 @: rAnswer: C. B+ D, b9 R( c8 g/ |
------------0 ~) Q0 ?* \8 U. F9 f8 d
Question 11+ F! r1 e+ X5 L1 I7 s2 j) S
Otherthan a working EIGRP configuration, which option must be the same on allrouters for EIGRP authentication key rollover to work correctly?' B/ _: }' j4 @
A. SMTP1 ~# [, l3 F1 W6 ^
B. SNMP
* a! y. b9 Q* W! O0 j0 N: H! h- JC. Passwords1 c* b; }( \) ]7 T) b
D. Time3 [4 a1 Q/ M! E" M+ l P6 R
Answer: D
2 T* f" H: @" Q" h------------- y% S7 q0 {; f( v9 f
Question 12
$ j" y: A( [+ _- O; U) eIfyou configure one router in your network with the auto-cost reference-bandwidth100 command, which effect on the data path is true?
& S5 ~) Y; X2 |; ^0 MA.The data path remains the same for all links
; B& T" d" w. N/ a; m8 U F" eB. Thedata path changes for 10Mbps links only; g7 F/ Z( N d4 p; g2 T0 q" H6 [5 K3 _
C. The datapath changes for all links
8 G% z1 H0 z3 F m- e$ Q% BD. Thedata path changes for 10Gbps links only" k8 @: Y, R2 x2 _% ^# n! N
Answer: A
E- H+ K: P/ O8 C; Z
有誰可以分享正確的答案
" }2 s) \4 G/ @- X( D9 T5 Q |